Tomcat modify cookies security
Modification method
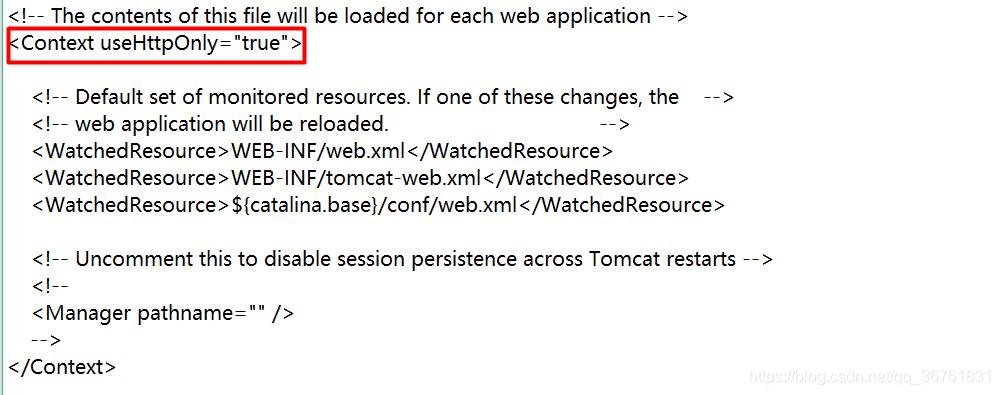
1. Enter the conf folder of Tomcat and open the context.xml file

2. Change the <Context> tag attribute to <Context useHttpOnly="true">:
Cookie common attributes
- Cookie name . The cookie name must use characters that can only be used in URLs, generally letters and numbers, and cannot contain special characters. If there are special characters, you want to transcode. For example, when js operates cookies, escape() can be used to transcode the name.
- Cookie value , the cookie value is the same as the name of the cookie, which can be transcoded and encrypted.
- Expires , expiration date, a time in GMT format, after this date, the browser will delete the cookie, when this is not set, the cookie will disappear after the browser is closed.
- Path , a path, the page below this path can access the cookie, generally set to "/" to indicate that all pages of the same site can access the cookie.
- Domain , subdomain, specify that the cookie can be accessed only under this subdomain. For example, to make the cookie accessible under a.test.com, but not under b.test.com, you can set the domain to a.test .com.
- Secure , security, specifies whether the cookie can only be accessed through the https protocol. General cookies can be accessed using the HTTP protocol. If Secure (no value) is set, the cookie can only be accessed by the page when the https protocol connection is used.
- HttpOnly , if the "HttpOnly" attribute is set in the cookie, the cookie information cannot be read by the program (JS script, Applet, etc.).
HTTPONLY
1. In order to solve the problem of XSS (cross-site scripting), IE6 began to support the HttpOnly attribute of cookies, which is currently supported by most browsers (IE, FF, Chrome, Safari). When the HttpOnly attribute in the cookie is set to true (the last 7th bit), the front-end script cannot access or manipulate the cookie (only through the background), so XSS is invalid. Browsers that support HttpOnly session cookies will only be used when sending HTTP (or HTTPS) requests, thereby restricting access from other non-HTTP APIs (such as JavaScript). This limitation is mitigated, but the threat of cookie theft via cross-site scripting (XSS) is not eliminated. This feature only works with session management cookies, not other browser cookies.
2. The function of httponly is to restrict access from other non-HTTP APIs (such as JavaScript). It is still possible for cookies to be intercepted and captured during the transmission process.
3. Setting the HttpOnly attribute to true does not prevent an attacker with access to the network channel from directly accessing the cookie. In this case, Secure Sockets Layer (SSL) should be considered to help. Workstation security is also important because malicious users may use open browser windows or computers that contain persistent cookies to gain access to a website under the identity of a legitimate user.
Summarize
Increase cookie security Add HttpOnly and secure attributes
(1) HttpOnly attribute: If the "HttpOnly" attribute is set in the cookie, the cookie information cannot be read by the program (JS script, Applet, etc.), which can effectively prevent XSS attacks.
(2) secure attribute: When set to true, it means that the created cookie will be transmitted to the server in a secure form, that is, it can only be passed by the browser to the server in the HTTPS connection for session verification. If it is an HTTP connection, then This information will not be passed, so the specific content of the cookie will not be stolen.
For the above two attributes, the secure attribute is to prevent information leakage after being monitored and captured during the transmission process. Position 6 is true. The purpose of the HttpOnly attribute is to prevent the program from attacking after obtaining the cookie. Position 7 is true.
Note: In order to reduce the damage caused by XSS cross-site scripting attacks, it is usually necessary to use HTTP-only cookies in combination with other techniques. Used alone, it is not comprehensive against cross-site scripting attacks.